Authorisation
The merchant’s payment terminal generates an authorisation request that is sent to the merchant’s acquirer, who in turn forwards it to the card scheme (Visa or Mastercard), from where it is sent to the issuer or the issuer’s processor.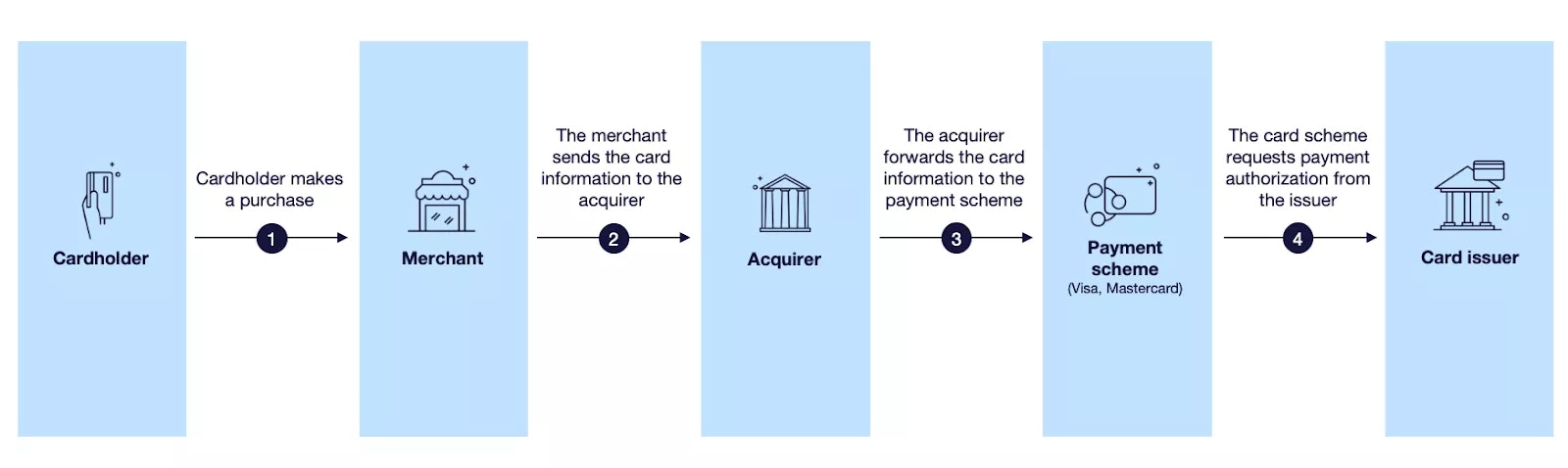
- The financial transaction is received or
- A reversal is received or
- Until the authorisation is cleared.
Authorisation processing at Enfuce
The authorisation process consists of three consecutive steps:- Technical validation
- Business validation
- Fraud validation
Technical validation
Technical validation refers to the practice of verifying that the security elements present in the authorisation message comply with the data and keys in the system. The technical validation of data elements is categorised based on whether the transaction is ‘Card present’ or ‘Card not present’. For ‘Card present’ transactions, the validation is determined by different security elements captured from the chip/magnetic stripe at the point of interaction. These validations include PIN, CVV/CVC, chip certificate, expiry date, card status etc. For ‘Card not present’ transactions, the chip/magnetic stripe cannot be read. There are other security elements to be verified, such as CVV2/ CVC2, CAVV/AAV (3D Secure validation), expiry date and card status. In case the verification of the technical authorisation gives a negative result, Enfuce will decline the authorisation and generate a response to the card scheme. In the next table, we describe the different technical validations which are performed. Data element validation for both ‘Card present’ and ‘Card not present’ instances| Data | Description |
|---|---|
| PAN | The following validations are done based on the PAN: Is the PAN an existing PAN within the system? If the PAN is non-existing, the authorisation will be declined. Luhn algorithm – does the check digit match with the rest of the PAN? |
| Expiry date | The system will check that the expiry date matches with the expiry date in Enfuce system |
| Data | Description |
|---|---|
| iCVV validation (cvc/cvv on chip) | Validation of the iCVV. If verification fails the authorisation request is declined. The purpose of the Integrated Chip Verification Value is to protect against the copying of the magnetic stripe data from the chip for creation of a counterfeit magnetic stripe card. The iCVV on the magnetic stripe data contained in the chip is different from the CVV1 value on the physical magnetic stripe. |
| Cryptogram validation (ARQC) | Validation of the Authorisation Request Cryptogram to check that the EMV chip has not been tampered with. If validation fails, the authorisation request is declined. |
| Track 1 data validation (magnetic stripe transactions) | Validate if track 1 data is included in the transaction if the Service Code indicates that data must be present. Validate that the CVV1/CVC1 of track 1 is correct. |
| Track 2 data validation (magnetic stripe transactions) | Validate that CVV1/CVC1 on track 2 of the magnetic stripe is correct. |
| Terminal verification result (TVR) | The issuer rules for Terminal Action Analysis are known as Issuer Action Codes (IACs). System will analyse the Issuer Action codes to check if the performed offline data authentication has failed. |
| Card verification result (CVR) | Validation of the Card Verification Result that resides in the EMV data |
| PIN Verification Service | PIN validation done by comparing against stored & encrypted value. (PVV might be used in some cases) |
| Card Sequence number | Validation of card sequence number. Note that previous sequence numbers can be used if card status allows it but not non-existing ones. |
| Data | Description |
|---|---|
| CVV2/CVC2 validation | Security code validation when using card in e-commerce environment. The card schemes will perform pre-validation and Enfuce will repeat the validation. |
| 3DS certificate validation (CAVV/AAV) | Verify that the authentication result value in CAVV/AAV field of the authorisation message matches the 3DS authentication value. Decline if not equal. |
Business validation
Business validation refers to the validating rules defined by yourself or your customer. These rules include, for example, card and account status, available balance and your advanced spend controls. If the business validation fails, Enfuce will decline the authorisation and generate a response to the card schemes. The following tables describe the different business rule validations for authorisations.Credit and debit cards
| Data | Description |
|---|---|
| Account and card statuses | Both the card and the account need to have the status ‘OK’ for the authorisation to be approved. Card status ‘Card no renewal’ is also considered OK. If the card or the account has any other status, the authorisation is declined. Also, a card can be blocked during delivery. Until the cardholder activates the card, authorisations are declined. In case there are several reasons for rejecting the authorisation, Enfuce will prioritise the card status when generating the response code: For example, if the customer enters the wrong PIN and has a blocked card, the response will be given based on the blocked card. See card and account sections for statuses. |
| Advanced spend controls | Spend controls will decline authorisations based on the rules set up per spend control. See the advanced spend controls section for more details. |
| Online PIN tries | Enfuce has an ‘Online PIN tries’ feature that will restrict the number of online PIN tries. |
| Available balance | Available balance needs to cover the settlement amount of the purchase plus fees and markup. See the description of available balance for more details. |
- Refund positive balance ‘RE’ (debiting)
- A refund positive balance transaction posted via the API will be rejected if there isn’t a sufficient amount of available balance.
- Prepaid top-up ‘TP’ (crediting)
- A Prepaid top-up transaction posted via the API will be rejected if the limits in the spend control for said transaction type have been reached.
Fraud validation
If both technical and business validations are successful, the authorisation request is forwarded to Enfuce (or external) fraud monitoring system for fraud validation. Fraud validation aims to reduce the risk of fraudulent activity that might result in financial losses and damage to reputation. As part of the fraud validation process, Enfuce also validates that customer authentication has been performed as required. Please see the Authentication guide for more details on these requirements. See more on the fraud section of our guide.Authorisation reversals and authorisation of credit transactions
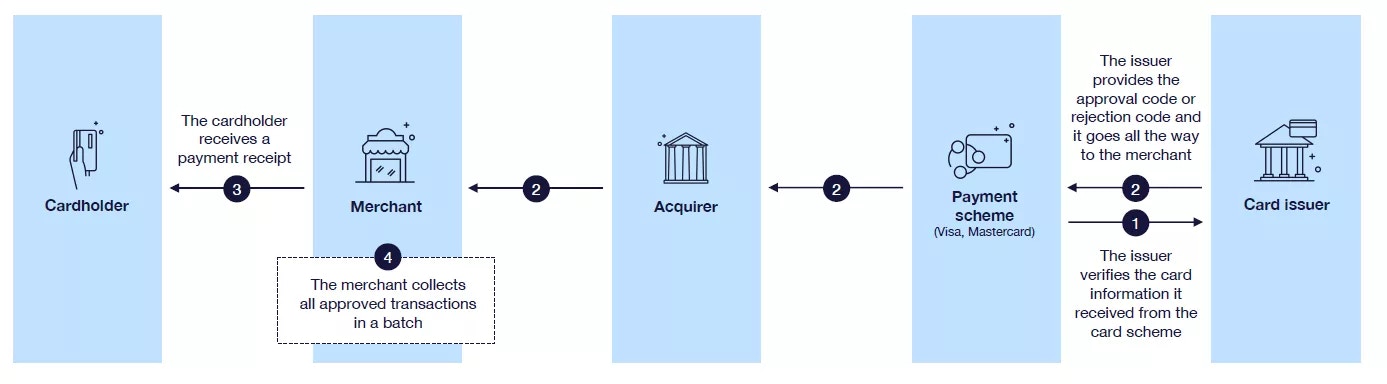
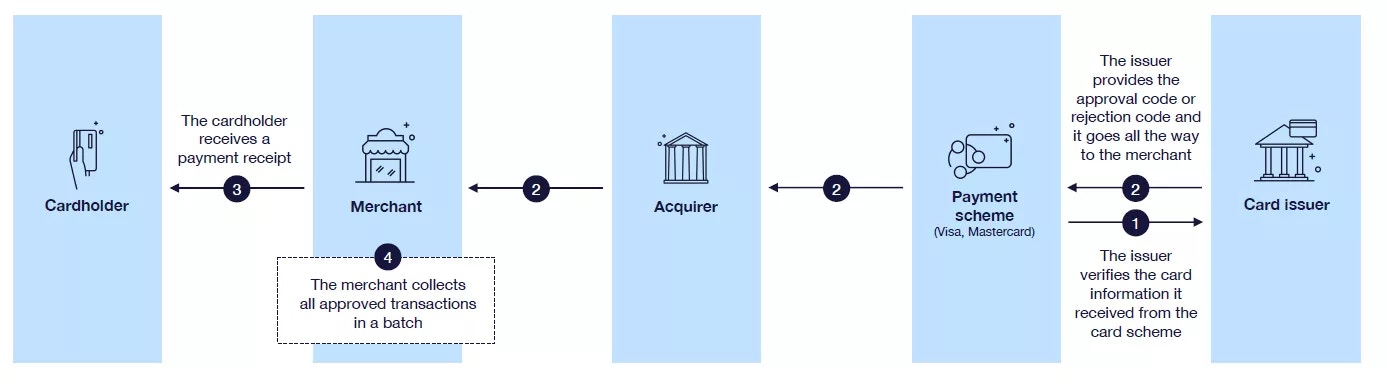
Merchants can reverse authorisations in cases where the financial transaction is not yet sent and the authorisation block is the only action done for the purchase. In this case, Enfuce receives an authorisation reversal and the original authorisation is reversed and the available balance is increased immediately. Merchants also send authorisations for credit transactions. Credit transactions can be purchase refunds or so-called ‘original credits’ like casino winnings. As per card scheme recommendation, these authorisations are treated as information of an upcoming credit. When the authorisation is processed, it does not increase the available balance until the financial transaction is processed.Authorisation response
After the authorisation processing is concluded, Enfuce generates a response that directs the merchant on how to proceed with the transaction. If validations are successful and the authorisation is approved, the purchase can be finalised. If the authorisation is declined, the merchant needs to discontinue the purchase or ask for an alternative payment method. The below table lists the different response codes used and their use case.Response codes
Please be aware that Visa and Mastercard impose a non-compliance fee on issuers if more than 5% of card-not-present transactions are declined with response code 05 (“Do Not Honor”). Therefore, generic response codes should be avoided when the specific reason for decline can be provided. From October 2025, Response code 57 must not be used by Visa issuers. Incorrect use of Response Code 57 will be reclassified to a generic decline response code (05).| Response code | Status | Description | Use case | Example | ||
|---|---|---|---|---|---|---|
| 0 | Approved | Approved/ Successfully completed | The transaction is successfully approved for the requested amount. | A customer makes a successful purchase using their card. | ||
| 1A | Declined | Additional Customer Authentication Required (VISA) | Authentication is required. If the transaction falls under PSD2 regulations and was not processed through 3D Secure, retry with 3D Secure. (Applicable only in the European region.) | A customer tries to complete an online purchase without passing 3D Secure authentication. | ||
| 3 | Declined | Invalid Merchant | Indicates that the purchases at this merchant (MID) or merchant category (MCC) is not allowed. | A purchase attempt is declined at a merchant not allowed by the issuer. | ||
| 4 | Declined | Pick up card | A Mastercard card has been reported as fraudulently used and must be picked up. | A customer tries to use a card that has been reported as fraudulently used. | ||
| 5 | Declined | Do not honor | The transaction was declined without a specific reason. Issuers should use this code only when no other, more specific decline reason applies, or when a technical issue prevents a proper response. Mastercard and Visa returns this code during Stand-In Processing, when the issuer is unresponsive or unavailable. This code may also be triggered by fraud prevention systems such as Fraud Rules Manager. | A cardholder attempts a transaction but it is refused without specifying why. | ||
| 5C | Declined | Transaction not supported / blocked by issuer | The transaction is not permitted to the cardholder (Applicable for Visa transactions only, can be used as an alternative to 57.) | A Visa issuer blocks a transaction that is not supported per internal policy. | ||
| N7 | Declined | CVC is wrong | A Visa authorization request did not pass CVV2 (Card Verification Value) verification. It is typically used in Card-Not-Present (CNP) transactions when the CVV2 provided by the cardholder does not match the issuer’s records. This code should not be used to decline transactions simply because the CVV2 was not provided. It applies only when a CVV2 is present but fails verification. | A Visa customer have entered wrong CVC number. | ||
| 9G | Declined | Blocked by cardholder / contact cardholder | Cardholder-initiated block; issuer declines authorization and requests contact with cardholder. | A customer’s card is self-blocked or flagged for confirmation, requiring issuer contact. | ||
| 10 | Approved | Approved for partial amount | The full amount cannot be approved due to insufficient funds or spending limits. Instead, a partial approval is granted. Only applicable if a merchant indicates that it accepts partial approvals. | A customer uses their card at an automatic fuel pump, but due to a spend limit, only part of the requested amount is approved. | ||
| 12 | Declined | Invalid Transaction | Incorrect or missing transaction details prevent authorization. From April 12 2025 for Visa: Use when a fatal technical error prevents approval including (e.g.-invalid POS entry mode for card type). May be used when ICC/CVV/CAM cryptogram validation fails or for invalid OCT or missing security data. | A Visa card’s chip cannot be read due to a broken POS chip reader and the terminal attempts to process the transaction using the magnetic stripe instead. | ||
| 13 | Declined | Invalid Amount | The transaction amount is not valid for processing. | A merchant tries to process a reversal but the reversal amount does not match the original authorization amount or the adjustment is bigger than than the original authorization amount. | A customer accidentally enters an incorrect card number during an online purchase, or fraudulent attempts are made to guess valid card numbers. | |
| 30 | Declined | Format error | The authorization message does not comply with format requirements. | The authorization message is sent in an incorrect format, causing the transaction to be rejected. | ||
| 41 | Declined | Lost card pick up | The card has been reported lost and must be picked up. | A lost card is used for a transaction and gets declined due to security measures. | ||
| 43 | Declined | Stolen card pick up | The card has been reported stolen and must be picked up. | A fraudster attempts to use a stolen card but it is already reported and declined. | ||
| 46 | Declined | Contract closed | A Visa authorization is declined when the card has been closed due to fraud. Effective 3th June 2025: A Mastercard authorization is declined when the credential or account is permanently closed and no further authorization will be approved. | Visa: A fraudster attempts to use a closed card. Mastercard: A cardholder tries to use a permanently closed card. | ||
| 51 | Declined | Not sufficient funds | The cardholder has insufficient funds to complete the transaction. | A customer attempts to purchase an item but does not have enough funds available. | ||
| 54 | Declined | Expired card | The card has expired and is no longer valid for transactions. | A cardholder tries to make a payment using an expired card. | ||
| 55 | Declined | PIN incorrect | The entered PIN is incorrect. | A customer enters the wrong PIN at an ATM, causing the transaction to fail. | ||
| 57 | Declined | Transaction not allowed for cardholder | An authorization is declined due to issuer or customer-set rules. Also applies when a Mastercard card or account is blocked for non-fraud reasons. From 18 October 2025, Visa reserves this code for Visa use only. | A customer tries to make an international transaction that is restricted on their card. A Mastercard cardholder attempts an e-commerce transaction using a card that has a restriction or block specifically set to prevent online transactions. | ||
| 58 | Declined | Transaction not allowed for merchant/terminal | The transaction is declined if the card does not allow the specified transaction type or if the type is unrecognized. Used when POS Entry Mode or terminal capability mismatches the transaction type as per issuer policy. | A merchant category is restricted from accepting transactions from a particular card type. May be used in the case of Mastercard fallback transactions. | ||
| 59 | Declined | Suspected fraud | The transaction is flagged as potential fraud and blocked. | A high-value purchase triggers the fraud detection system and the transaction is blocked. | ||
| 61 | Declined | Exceeds withdrawal amount limit | The transaction exceeds the allowed spending limit. | A customer tries to withdraw more money from an ATM than their daily limit allows. | ||
| 62 | Declined | Restricted card | A transaction is declined due to a suspended card token. This code is also used for Visa cards to indicate a decline due to country restrictions. For Mastercard, it is used when the account or card is temporarily blocked. | A transaction is declined when a merchant attempts to charge a saved card token (‘card on file’) that is suspended. | ||
| 63 | Declined | CVC is wrong | Used to indicate that Mastercard Authorization request didn’t pass CVV2 verification. | A Mastercard transaction customer has entered wrong CVC number. | ||
| 65 | Declined | Activity count limit/Withdrawal frequency limit exceeded | A transaction may be declined if a spend control or contactless counter restricts usage or if authentication—such as 3D Secure (3DS) or PIN—is required. If PSD2 Strong Customer Authentication (SCA) applies and was not used, retry the transaction with 3DS. | A customer attempts too many contactless Mastercard transactions without PIN verification. A Mastercard customer inserts their card into a chip terminal but the terminal does not prompt for a PIN when it should. | ||
| 70 | Declined | Invalid transaction; contact card issuer (VISA) | Visa-specific code used when a contactless transaction is declined due to a usage counter limit and/or required PIN data is not included in the authorization request. | A customer attempts too many contactless Visa transactions without PIN verification. A Visa cardholder inserts their chip card into a terminal, but the terminal fails to prompt for a PIN when required. | ||
| 71 | Declined | PIN not changed | The PIN change transaction was declined, and the PIN was not updated. | The customer attempted to change their card PIN, but the PIN change was not completed. | ||
| 72 | Declined | Locked card (Mastercard) | Effective June 3, 2025: Mastercard code for payment declined due to the account not being activated (e.g., newly issued card). | A cardholder attempts to use a new card that has not yet been activated. | ||
| 75 | Declined | Allowable number of PIN tries exceeded | The cardholder has exceeded the maximum allowed PIN attempts. | A cardholder enters their PIN incorrectly multiple times, locking the card. | ||
| 76 | Declined | Wrong PIN, number of PIN tries exceeded | The cardholder has exceeded the allowed number of incorrect PIN attempts. | The cardholder has entered the wrong PIN too many times. | ||
| 78 | Declined | Record Not Found (VISA) | An authorization is declined due to issuer or customer-set rules. This also applies when a Visa card or account is blocked for reasons unrelated to fraud. Additionally, it is used for declines related to the reminder process on a credit product. | A cardholder tries to use a blocked credit card, and the authorization request is rejected. | A blocked Visa credit card is used and the transaction is declined. | |
| 81 | Declined | Foreign network error | The transaction fails due to an issue in the payment network, reported in advices by the scheme. | A transaction fails due to a network error. | ||
| 82 | Declined | Time-out at issuer system / Bad CVV | The transaction is declined during stand-in processing when CVV security value validation fails. For Mastercard indicates a timeout at the issuer during the original authorization request. Also appears in reversal advices. For Visa Returned during stand-in processing if CVV/CAM/CAVV/iCVV/dCVV2 validation fails. Can also result from an interrupted offline PIN authentication. | A customer enters an incorrect CVV during an online purchase while stand in processing in active, causing the payment to fail. | A customer enters an incorrect CVV during a stand-in processed online purchase. | |
| 85 | Approved | No reason to decline | Zero-amount authorization request validates the card number without holding funds. Approval or ‘no reason to decline’ may be returned. | A card verification request is processed successfully without fund hold. | ||
| 86 | Declined | Cannot verify PIN | The transaction is declined during stand-in processing when PIN validation fails or cannot be completed by the card scheme. | A cardholder attempts a cash withdrawal, but the PIN validation system is unavailable. | ||
| 91 | Declined | Issuer unavailable | The external ledger is unavailable to process the authorization request. Mastercard invokes Stand-In; Visa does not unless N0 is used. | A transaction fails because the issuer’s system is temporarily offline. | ||
| 93 | Declined | Cannot be completed, violation of law | Used for regulatory blocks, e.g., gambling, non-opt-in CNP, or missing second-factor auth for domestic e-commerce. | A cardholder is blocked from online transactions due to legal or compliance rules. | ||
| 94 | Declined | Duplicate transaction | A merchant resends an authorization that was already processed. | A repeated authorization request is declined as a duplicate. | ||
| 95 | Declined | No authorization to match | The authorization cannot be matched to a previous transaction and thus cannot be reversed. | A reversal is attempted without a matching original transaction. | ||
| 96 | Declined | System malfunction | A system issue prevents processing or exceeds scheme response time limits. | A transaction fails due to internal processing error. | ||
| N0 | Declined | Issuer unavailable | Used when Visa forces single-request Stand-In Processing, converting 91 or 96 to N0. | A transaction fails due to the issuer being offline, triggering Visa STIP. |
Advanced spend control response codes
The following response codes are returned when a payment is declined due to a limit rule set up via advanced spend controls. (This service is sold separately.)| Response code | Status | Description | Use case | Example |
|---|---|---|---|---|
| 03 | Declined | BLOCKED_MERCHANT | Declined due to merchant restrictions set by spend control rules. | A transaction is declined at a merchant that violates issuer’s spend control policy. |
| 57 (Mastercard) | Declined | BLOCKED_COUNTRIES | Declined due to country restrictions set by spend control rules. | A Mastercard transaction is blocked due to country-based spend control restrictions. |
| 62 (Visa) | Declined | BLOCKED_COUNTRIES | Declined due to country restrictions set by spend control rules. | A Visa transaction is blocked due to issuer-defined country restrictions. |
| 61 | Declined | AMOUNT | Declined due to an amount limit set by spend control rules. | A transaction amount exceeds the limit set by the cardholder’s or issuer’s spend controls. |
Response codes currently not in use
Some response codes from card schemes are defined but not widely used. These codes are often reserved for future scenarios or specific edge cases, and as such, they rarely appear in active transactions. Below is a table listing these response codes and their potential use cases.| Response code | Status | Description | Use case | Example |
|---|---|---|---|---|
| 15 | Declined | No Such Issuer | First 8 digits of the account number do not relate to an issuing identifier. Reattempt not permitted with same PAN or token. | A card number is entered for a BIN or account range not recognized in Visa’s systems. |
| 1 | Declined | Refer to card issuer | Used only by non-Visa and Japan domestic transactions. Converted to 05 in Visa systems. | Cardholder must contact issuer for details; Visa sends 05 instead. |
| 2 | Declined | Refer to Card Issuer, special condition | Codes 01 and 02 can only be used by non-Visa transactions and Japan domestic transactions. Not returned in response; converted to 05 instead and 05 sent to Schema. | |
| 6 | Declined | Error | ||
| 7 | Pick up | Pick up card, special condition | ||
| 8 | Approved | Honor with identification | ||
| 9 | Declined | Request in progress | ||
| 11 | Approved | Approved (VIP) | Not returned in response; converted to 00. | A VIP transaction is internally approved but translated to generic approval (00) in Visa systems. |
| 15 | Declined | No such issuer | ||
| 17 | Declined | Customer cancellation (0400 only) | ||
| 19 | Declined | Re-enter transaction | ||
| 21 | Declined | No action taken | ||
| 25 | n/a. | No such record (MTI 0312) | ||
| 26 | n/a. | Duplicate record update, old record replaced (MTI 0312) | ||
| 27 | n/a. | File update field edit error (MTI 0312) | ||
| 28 | n/a. | File locked out while update (MTI 0312) | ||
| 29 | n/a. | File update error, contact acquirer (MTI 0312) | ||
| 32 | Declined | Completed partially (MTI 0400 only) | ||
| 34 | Declined | Suspect Fraud (MTI 0400 only) | ||
| 40 | n/a. | Requested function not supported (MTI 0312) | ||
| 52 | Declined | No checking account | ||
| 53 | Declined | No savings account | ||
| 64 | Declined | Wrong original amount | Transaction does not fulfill AML (Anti-Money Laundering) requirements. | The original amount submitted does not match what was expected per AML criteria. |
| 68 | Declined | Response received too late | Should only be used in Authorization Negative Acknowledgement (0190) responses. Converted to 05 otherwise. | A late response triggers a decline; Visa sends 05 to schema instead. |
| 80 | Declined | Network error | No financial impact. Used in reversal responses to declined originals. | A system issue causes network error response, often in the context of reversal messages. |
| 83 | Declined | Transaction failed | ||
| 84 | Declined | Pre-authorisation time too great | ||
| 88 | Declined | Cryptographic failure | Mastercard-only decline code used for crypto validation errors. | A cryptographic check fails during Mastercard authorization, leading to a decline. |
| 92 | Declined | Invalid receiving institution id |
Understanding Payment Declines and Response Descriptions
When a payment is declined, besides the response code, if available for the specific payment, there is also a response description that provides more context about why the transaction failed. This description includes a return code and a short explanation, and it can be accessed it via our transaction endpoint. In some cases, multiple issues might cause a decline. However, because only one response code can be sent to the card network and the payment terminal, our system must determine which reason to prioritize. This decision is made using a built-in prioritization logic.Overview of Decline Reason Prioritization
Here’s a simplified overview of how these reasons are prioritized:- Technical Issues
- Card/account is blocked or closed
- Invalid CVV or expiration date
- Wrong PIN
- Token is disabled
- Business Rules
- Transactions blocked in specific countries
- Spending limits (e.g., monthly cap)
- Fraud Detection
- Fallback declines
- The cardholder enters the wrong PIN (
055 – Incorrect PIN) - The monthly spending limit is exceeded (
061 – Usage Limit "MONTHLY_ALL" Amount Exceeded)
- The response description shown in the transaction endpoint will refer only to the wrong PIN.
- The response code sent to the card scheme will also be 55, corresponding to the incorrect PIN.
Response descriptions
The most common descriptions are listed below:| Response description (return code) | Possible action |
|---|---|
| 003-Device ID is not on file | Card device not recognized. Please try again. |
| 003-Usage Limit “BLOCKED_MCC” Response | This merchant type is blocked for your card. |
| 003-Usage Limit “MONBLOCKED_MCC” Response | This type of merchant is blocked for your card. |
| 004-PICK UP | Your card can’t be used. Please contact your bank. |
| 005-CAVV is wrong | Incorrect security code (CAVV). Please check and try again. |
| 005-CVC is wrong | Incorrect security code (CVC). Please check and try again. |
| 005-Do not Honour | Declined due to unspecified error. |
| 005-EMV has not passed verification | Security verification failed. Please try again. |
| 005-Outward Response Code | Declined due to unspecified error. |
| 005-The maximum number of authorized tokens has been reached | Card cannot be used — token limit reached. |
| 005-Token is disabled. | This card is no longer active. |
| 005-Usage Limit “card_part_grade” Response | Your card cannot be used for this type of payment. |
| 005-Usage Limit “CASH_BLOCK_MCC” Response | This card can’t be used for cash withdrawals for this merchant. |
| 005-Usage Limit “RETAIL_BLOCK_MCC” Response | This merchant type is not supported for your card. |
| 006-Error | A system error occurred. Please try again later. |
| 012-Invalid Currency | This currency is not supported. |
| 012-Invalid DCVV data | Card security data is invalid. Please try again. |
| 012-Invalid symbol in track data | Card data unreadable. Try again or use a different method. |
| 012-Invalid track format | There was an issue reading your card. Try again or use another payment method. |
| 012-PAN and PAN from track mismatch | Card details couldn’t be verified. Please try again. |
| 012-Transaction not allowed | This type of transaction is not permitted. |
| 014-Active plastic not found | This card isn’t active. |
| 014-Card locked | Your card is locked and cannot be used. |
| 014-Card number not on file | Your card is not recognized. Please check the details. |
| 014-Contract is closed | This card account is closed and cannot be used. |
| 014-Incorrect token to card link | A system error occurred. Please try again later. |
| 014-Invalid card expiry date or not active plastic | Invalid card details. Please check your expiry date or card status. |
| 014-Invalid Contract Status | Your card account status prevents this transaction. |
| 014-No such card | This card isn’t recognized. Please check the details. |
| 030-Format error | There was a system error. Please try again. |
| 041-Invalid Contract Status | Your card account is not active. Please contact your bank. |
| 041-Pick up, lost card | Your card has been reported lost. Contact your bank. |
| 043-Invalid Contract Status | Your card account status prevents this transaction. |
| 043-Pick up, stolen card | Your card was reported stolen. Contact your bank. |
| 051-Not sufficient funds | Not enough money in your account. |
| 051-Not sufficient funds available | Not enough money in your account. |
| 051-Transaction Declined | Your bank declined the payment. |
| 054-Card expiry date different than on file | Card expiry doesn’t match. Please check your card. |
| 054-Card locked | Your card is locked and cannot be used. |
| 054-Expired card / target | Your card has expired. |
| 054-Plastic is not on file | Invalid card details. Please check your expiry date or card status. |
| 054-The card has expired | Your card has expired. |
| 055-Incorrect PIN | Incorrect PIN. Please try again. |
| 055-PIN is wrong | Incorrect PIN. Please try again. |
| 057-Contract closed | This card account is closed and cannot be used. |
| 057-Invalid Contract Status | Your card account status prevents this transaction. |
| 057-Invalid Main Contract Status | Your card account status prevents this transaction. |
| 057-Outward Response Code | This transaction isn’t allowed with your card. |
| 057-Service declined for this Card | This transaction was declined because it is not allowed for the card. |
| 057-Service not allowed for this Card | This transaction was declined because it is not allowed for the card. |
| 057-Transaction Not Permitted | This transaction isn’t allowed with your card or the transaction was declined due to using the magnetic stripe instead of the chip reader. |
| 057-Usage Limit “AFRICA_BLOCK” Response | Your card can’t be used in Africa. |
| 057-Usage Limit “ASIA_BLOCK” Response | Your card can’t be used in Asia. |
| 057-Usage Limit “AUTH_BLOCK” Response | This payment type is not allowed for your card. There might be overdue balances on the account. |
| 057-Usage Limit “BALINQ_FEE” Response | Balance inquiry is not allowed on your card. |
| 057-Usage Limit “BLOCKED_MCC” Response | This type of merchant is not allowed for your card. |
| 057-Usage Limit “CONTACTLESS_BLOCK” Response | Contactless payments are blocked for your card. |
| 057-Usage Limit “ECOM_BLOCK” Response | Online payments are blocked for your card. |
| 057-Usage Limit “EUROPE_BLOCK” Response | Your card can’t be used in Europe. |
| 057-Usage Limit “HOME_BLOCK” Response | Your card can’t be used in your home region. |
| 057-Usage Limit “MONBLOCKED_MCC” Response | This type of merchant is blocked for your card. |
| 057-Usage Limit “NORTH_AMERICA_BLOCK” Response | Your card can’t be used in North America. |
| 057-Usage Limit “OCEANIA_BLOCK” Response | Your card can’t be used in Oceania. |
| 057-Usage Limit “SOUTH_AMERICA_BLOCK” Response | Your card can’t be used in South America. |
| 057-Zero Amount not allowed | Transactions for zero amount are not allowed. |
| 059-Invalid Contract Status | Your card account status prevents this transaction. |
| 059-Suspected fraud | Transaction declined due to suspected fraud. |
| 061-Exceeds withdrawal amount limit | You’ve exceeded your withdrawal amount limit. |
| 061-Usage Limit “24H_ALL” Amount Exceeded | You’ve reached your 24 h transaction limit. |
| 061-Usage Limit “24H_ATM” Amount Exceeded | You’ve reached your 24 h ATM withdrawal limit. |
| 061-Usage Limit “24H_RETAIL” Amount Exceeded | You’ve reached your 24 h retail spending limit. |
| 061-Usage Limit “ANNUAL_YEARLY_ALL” Amount Exceeded | You’ve reached your spending limit for this calendar year. |
| 061-Usage Limit “ANNUAL_YEARLY_ATM” Amount Exceeded | You’ve reached your spending limit for this calendar year. |
| 061-Usage Limit “ANNUAL_YEARLY_RETAIL” Amount Exceeded | You’ve reached your spending limit for this calendar year. |
| 061-Usage Limit “ROLLING_YEARLY_ALL” Amount Exceeded | You’ve reached your spending limit for the past 12 months. |
| 061-Usage Limit “ROLLING_YEARLY_ATM” Amount Exceeded | You’ve reached your spending limit for the past 12 months. |
| 061-Usage Limit “ROLLING_YEARLY_RETAIL” Amount Exceeded | You’ve reached your spending limit for the past 12 months. |
| 061-Usage Limit “BALANCE_LIMIT” Response | You’ve reached your balance limit. |
| 061-Usage Limit “CONTACTLESS_COUNTER” Amount Exceeded | You’ve reached your contactless payment limit. |
| 061-Usage Limit “DAILY_ALL” Amount Exceeded | You’ve reached your daily spending limit. |
| 061-Usage Limit “DAILY_ATM” Amount Exceeded | You’ve reached your daily ATM withdrawal limit. |
| 061-Usage Limit “DAILY_RETAIL” Amount Exceeded | You’ve reached your daily retail spending limit. |
| 061-Usage Limit “DAILY_TOP_UP” Amount Exceeded | You’ve reached your daily top-up limit. |
| 061-Usage Limit “MONTHLY_ALL” Amount Exceeded | You’ve reached your monthly spending limit. |
| 061-Usage Limit “MONTHLY_ATM” Amount Exceeded | You’ve reached your monthly ATM withdrawal limit. |
| 061-Usage Limit “MONTHLY_REFUND_POS_BAL” Amount Exceeded | Too many refunds this month. Please try again later. |
| 061-Usage Limit “MONTHLY_RETAIL” Amount Exceeded | You’ve reached your monthly retail spending limit. |
| 061-Usage Limit “MONTHLY_TOP_UP” Amount Exceeded | You’ve reached your monthly top-up limit. |
| 061-Usage Limit “WEEKLY_ALL” Amount Exceeded | You’ve reached your weekly spending limit. |
| 061-Usage Limit “WEEKLY_ATM” Amount Exceeded | You’ve reached your weekly ATM withdrawal limit. |
| 061-Usage Limit “WEEKLY_RETAIL” Amount Exceeded | You’ve reached your weekly retail spending limit. |
| 062-Restricted card | Your card is restricted and cannot be used. |
| 062-Usage Limit “AFRICA_BLOCK” Response | Your card can’t be used in Africa. |
| 062-Usage Limit “ASIA_BLOCK” Response | Your card can’t be used in Asia. |
| 062-Usage Limit “CASH_BLOCK_MCC” Response | Your card is blocked for cash transactions. |
| 062-Usage Limit “ECOM_BLOCK” Response | Online payments are blocked for your card. |
| 062-Usage Limit “EUROPE_BLOCK” Response | Your card can’t be used in Europe. |
| 062-Usage Limit “HOME_BLOCK” Response | Your card can’t be used in your home region. |
| 062-Usage Limit “NORTH_AMERICA_BLOCK” Response | Your card can’t be used in North America. |
| 062-Usage Limit “OCEANIA_BLOCK” Response | Your card can’t be used in Oceania. |
| 062-Usage Limit “SOUTH_AMERICA_BLOCK” Response | Your card can’t be used in South America. |
| 065-Exceeds withdrawal frequency limit | Declined due to an activity limit is exceeded or Authentication (PIN or 3DS) is needed. |
| 065-Usage Limit “24H_ACC_ALL” Number Exceeded | Too many account transactions today. Try again later. |
| 065-Usage Limit “24H_ALL” Number Exceeded | You’ve made too many transactions today. |
| 065-Usage Limit “24H_ATM” Number Exceeded | You’ve made too many ATM withdrawals today. |
| 065-Usage Limit “24H_RETAIL” Number Exceeded | Too many purchases today. Please try again tomorrow. |
| 065-Usage Limit “CONTACTLESS_COUNTER” Number Exceeded | Too many contactless transactions. Try chip or swipe. |
| 065-Usage Limit “DAILY_ALL” Number Exceeded | Too many transactions today. Please try again tomorrow. |
| 065-Usage Limit “DAILY_RETAIL” Number Exceeded | You’ve made too many retail purchases today. |
| 065-Usage Limit “ECOM_BLOCK” Response | Online payments are blocked for your card. |
| 065-Usage Limit “MONTHLY_ALL” Number Exceeded | You’ve made too many transactions this month. |
| 065-Usage Limit “MONTHLY_ATM” Number Exceeded | You’ve made too many ATM withdrawals this month. |
| 065-Usage Limit “MONTHLY_REFUND_POS_BAL” Number Exceeded | Too many refunds this month. Please try again later. |
| 065-Usage Limit “MONTHLY_RETAIL” Number Exceeded | You’ve made too many purchases this month. |
| 065-Usage Limit “SBT_ FULL_ GRADE_ DECLINE” Number Exceeded | Payment declined: PIN not entered. Please try again and enter your PIN. |
| 065-Usage Limit “WEEKLY_ALL” Number Exceeded | You’ve made too many transactions this week. |
| 065-Usage Limit “WEEKLY_ATM” Number Exceeded | You’ve made too many ATM withdrawals this week. |
| 065-Usage Limit “WEEKLY_RETAIL” Number Exceeded | You’ve made too many purchases this week. |
| 070-Usage Limit “CONTACTLESS_COUNTER” Response | You’ve reached your contactless payment limit without Cardholder Verification Method (CVM). |
| 070-Usage Limit “CVR 1” Response | This transaction was blocked for security reasons. |
| 070-Usage Limit “SBT_ FULL_ GRADE_ DECLINE” Response | Payment declined: PIN not entered. Please try again and enter your PIN. |
| 075-Allowed number of PIN tries exceeded | Too many incorrect PIN attempts. |
| 075-Allowed PIN Attempts exceeded | Too many incorrect PIN attempts. |
| 078-Invalid Contract Status | This transaction is not allowed with the current card status. |
| 078-Record Not Found | Transaction not allowed. Please try again later. |
| 078-Usage Limit “AUTH_BLOCK” Response | This payment type is not allowed for your card. |
| 082-Autonomus mode disabled | There was a system error. Please try again. |
| 082-Call to member timeout | There was a system error. Please try again. |
| 082-Time-out at issuer system | There was a system error. Please try again. |
| 086-Unable to validate PIN | PIN verification failed. Please try again. |
| 088-Key data is missing for CRYPTOGRAM verification | Security verification failed. Try again. |
| 091-Autonomus mode disabled | There was a system error. Please try again. |
| 091-Issuer or switch is inoperative | There was a system error. Please try again. |
| 096-System Malfunction | There was a system error. Please try again. |
Stand-in Processing (STIP)
Stand-in processing is a card scheme service that responds to authorisation requests on behalf of the issuer. STIP is used when the issuer (or issuer processor) is not available to respond to the authorisation request. STIP responds only when the issuer does not respond, is unavailable, cannot be reached, or when it provides an invalid response. The STIP parameters and limits are defined in the card scheme and they determine which authorisations can be approved even when the issuer is unavailable. The available parameters and limits differ depending on the product type (credit/debit/prepaid). If a BIN sponsor is used, the BIN sponsor will define the limits for STIP. The card scheme sends advice messages to inform the issuer of the authorisations that they have processed (both approved and declined) during the unavailability period. Enfuce processes and captures these advice messages after connections are re-established and adjust the available balances accordingly. In the scope of authorisation control and authorisation notifications, the STIP advice messages are treated like authorisation requests and will trigger webhook messages to the issuer.Authorisation notifications
A notification can be triggered by Enfuce for each authorisation after the processing has been completed. The notification provides a real-time message that a transaction has been completed (or attempted) with the card. The notification can be used to confirm a successful/declined authorisation to the customer. The notifications are not queued and cannot therefore be re-generated if missed. See our API documentation for more information on the content of each notification message.Authentication
Requirements for authentication
There are two main drivers for authentication during the transaction flow:- EU Revised Directive on Payment Services (PSD2)
- Card scheme requirement to authenticate
| Category | Description | Example |
|---|---|---|
| Knowledge | Something only the payer knows | A password, PIN |
| Possession | Something only the payer has | A chip card, pre-registered mobile phone |
| Inherence | Something the payer is | Biometric factors (facial recognition, fingerprint, voice recognition) |
- Decline authorisations originating from the EEA area that have not been verified by SCA and to which the exemptions do not apply.
- Approve authorisations originating from the EEA area that have not been verified by SCA but to which exemptions apply.
- Not require 3DS authentication for e-commerce transaction that have been flagged by merchants as exempt or are low value purchases.
- The acquirer country defines whether the transaction is performed within EEA. The merchant country can be different from the acquirer country. If the acquirer country is outside EEA, then the SCA mandate does not apply.
- For API-triggered transactions, the issuer is responsible for meeting the SCA requirements. Enfuce will not perform any validation and assumes that required authentications are performed.
Strong Customer Authentication (SCA) exemptions
SCA exemptions are defined based on the level of risk, amount, recurrence and the payment channel used for the execution of the payment. These exemptions aim to achieve the right balance between convenience of the payment experience and fraud reduction.- Contactless transactions with a low value
- Unattended transport and parking terminals
- Merchant category codes to whom this applies:
- 4111 (Transportation – Suburban and Local commuter passenger, incl ferries)
- 4112 (Passenger railways)
- 4131 (Bus lines)
- 4784 (Bridge and Road Fees, Tolls)
- 4789 (Transportation Services)
- 7523 (Automobile parking lots and garages)
- Merchant category codes to whom this applies:
- Trusted beneficiaries
- Your customer can whitelist merchants they trust.
- Enfuce does not currently support this.
- Recurring transactions
- This has to be marked as recurring by the merchant and a trace ID is present to ensure that first transaction has been authenticated
- Merchant-initiated transaction
- For merchant-initiated transactions, SCA will be required for the first payment. So long as the subsequent payments are initiated by the merchant, further SCA will not be required so long as the amounts being charged are within the reasonable expectation of the end customer.
- Low fraud – Transaction Risk Analysis
- If the payment service provider’s (acquirer or issuer) fraud rates are below set thresholds, this exemption can be evoked. The party that evokes the exemption also assumes the risk of not authenticating.
- Can be overruled by the other party, i.e., the acquirer may apply the exemption, but the card issuer can overrule.
- Low-value payment (acquirer or issuer)
- Enfuce has set up an issuer low-value limit of 30€ (or equivalent amount) for e-com transaction
- Can be overruled by the other party, i.e. the acquirer may apply the exemption, but the card issuer may overrule.
- Mail order or telephone order transactions
- Secure corporate payments
- Under the SCA-RTS Article 17, PSPs are allowed not to apply SCA for payments made by payers who are both legal persons and not consumers. This is only the case where the payments are initiated electronically through dedicated payment processes or protocols that are not available to consumers. This is subject to the view of local regulators.
- Card payments done with corporate cards through the global card schemes do not fall under the exemption.
Authentication at a physical location
There are multiple ways to perform an authentication if the purchase is completed at a physical location.- Chip & PIN: If the customer uses a physical card at the point of sale, the authentication is performed with the chip card (possession) and PIN (knowledge). It should be noted that magnetic stripe is not considered safe enough according to today’s regulations (i.e., it’s not proof of something you have) because they are so easy to copy. The same applies to signatures.
- Digital wallets: Digital wallets require the customer to authenticate before the purchase by opening the digital wallet. The tokenised card in the wallet (possession) becomes available with a security code (knowledge) or a biometric identifier like fingerprint or facial recognition (inherence).
- Biometric cards: If a customer has a biometric card (possession), the authentication is done through a fingerprint sensor right on the card body (inherence).

